Microsoft’s support representative shared details with Windows Latest on how Windows 11 24H2 reduces “requirements” to use BitLocker encryption, which means more PCs are now eligible for automatic and manual encryption. This is internally referred to as Auto_DE, where the “auto” is automatic, and DE most likely refers to Device Encryption.
Starting with Windows 11 version 24H2, the update removes the need for certain hardware features that were previously required for automatic encryption. For example, the update no longer requires devices to have Hardware Security Test Interface (HSTI) or Modern Standby.
For those unaware, Modern Standby is one of the flagship features of premium devices, which allow devices to instantly turn on and turn off like a mobile device. It was also a requirement for Windows 11’s device encryption, but that’s no longer the case, which means older hardware are also eligible for automatic or manual encryption.
Additionally, Windows 11 24H2 removes the need to check for untrusted Direct Memory Access (DMA) interfaces, which means manufacturers no longer need to add specific settings in the system registry.
These changes automatically update the requirements in the Hardware Lab Kit (HLK) tests, so manufacturers do not need to do anything extra to meet the new standards.
Bitlocker is turned on during the reinstallation of Windows 11 24H2, whether you like it or not.
BitLocker isn’t a new feature, and it’s typically turned on by default in Windows 11 version 23H2 on new flagship products, such as the HP Spectre.
Currently, it’s not turned on by default for most devices, but this changes with Windows 11 24H2, which turns on encryption automatically during reinstallation.
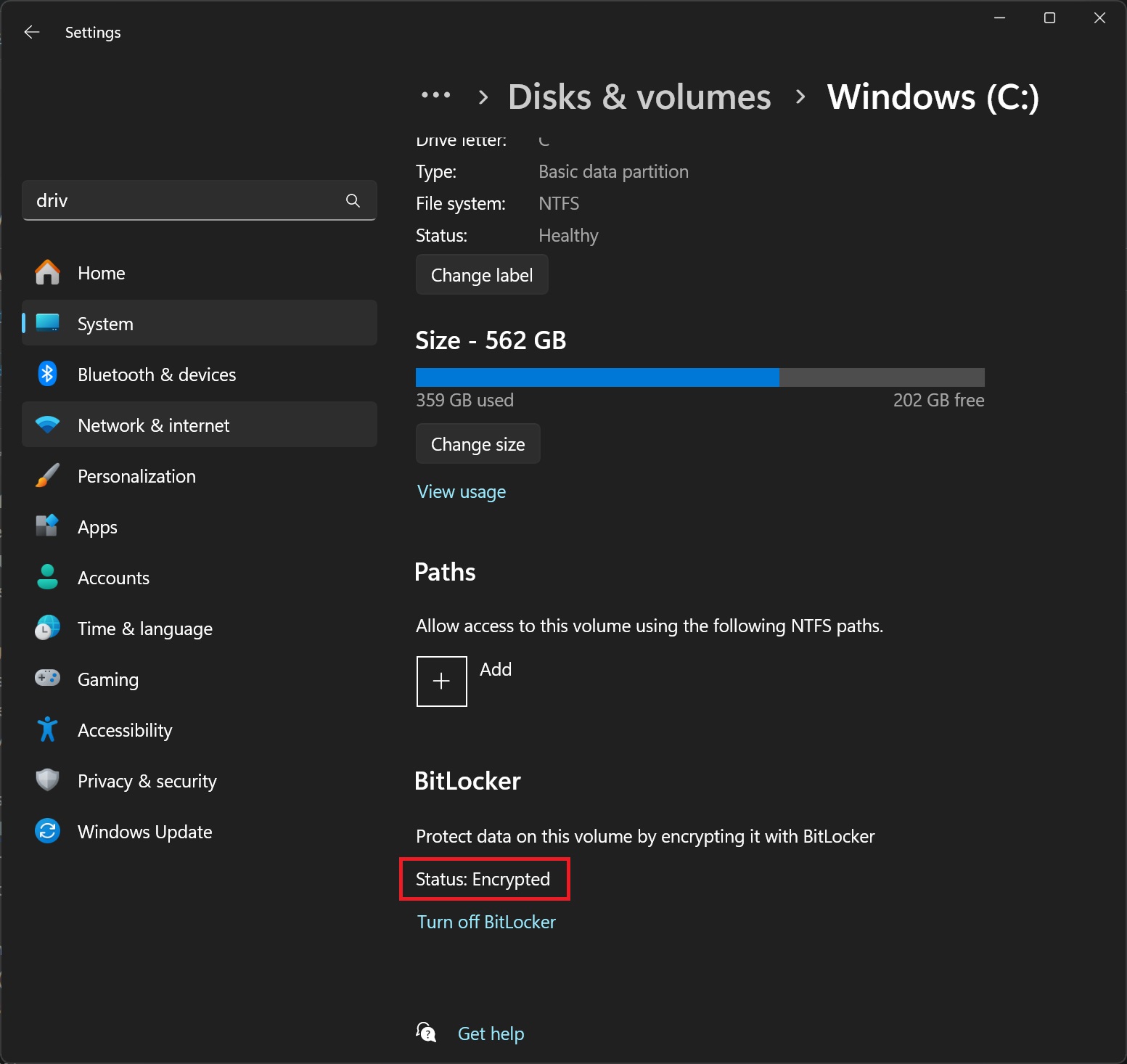
During the Windows 11 24H2 fresh/clean installation process, BitLocker encryption is enabled in the background, not just on Windows 11 Pro or higher editions but also on Windows 11 Home if the manufacturer has set a flag in the UEFI.
This encrypts all drives on the hardware and affects two editions of Windows 11: Home and Pro (Professional).
It does not affect devices upgraded to Windows 11 24H2 using Windows Update.
For encryption to be enabled automatically, the device needs to have a Trusted Platform Module (TPM) and UEFI Secure Boot, which are also required by Windows 11 as minimum hardware requirements.
Previously, devices also needed to meet Modern Standby or HSTI standards and ensure there were no untrusted DMA interfaces, but these requirements have been dropped in the Windows 11 24H2.
While automatic encryption starts during setup, it is only fully activated after the user signs in with a Microsoft Account.
Devices using local accounts won’t have automatic encryption, but users can still manually turn on BitLocker through the Control Panel.
The good news is that disabling BitLocker encryption during a reinstallation isn’t difficult.
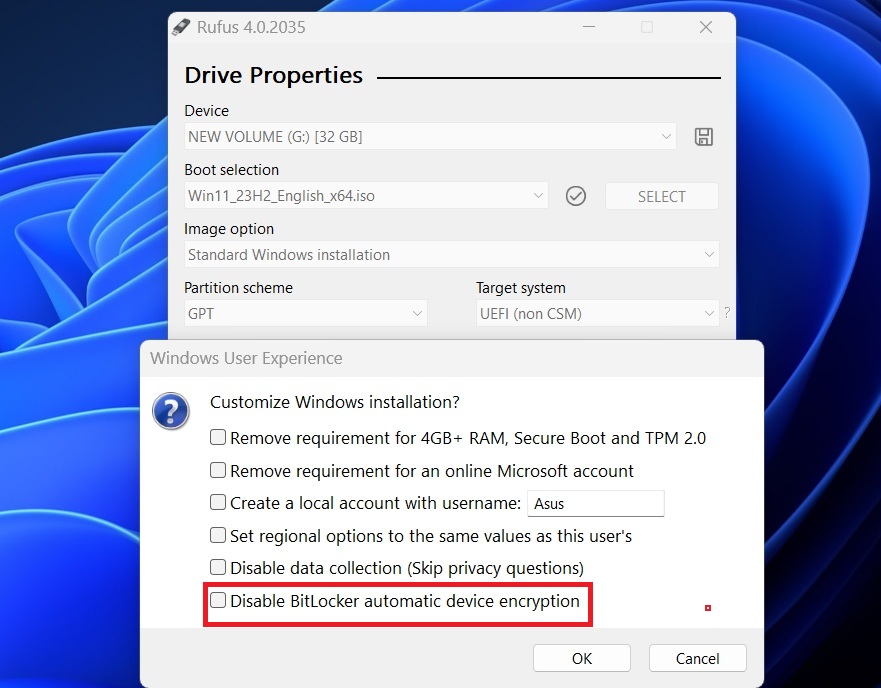
The easiest method is to create a bootable ISO through Rufus USB, which has the ability to disable Windows 11 24H2’s drive encryption.
Another method is to disable automatic encryption right from the installation wizard. To do this, open the Registry through the command prompt (Shift + F10) and change the BitLocker “PreventDeviceEncryption” key to 1.
Windows 11 24H2 is set to begin shipping on Intel and AMD PCs in the second half of the year, with our sources suggesting a late September or early October window.
The post Windows 11 24H2 reduces BitLocker eligibility, turns on automatic encryption for more PCs appeared first on Windows Latest
